THREAT INTEL: SOLARWINDS – The world’s most invasive and destructive Cyberattack, to date.
June 11, 2024Gibraltar: Tuesday 11 June 2024 at 07:40 CET
THREAT INTEL: SOLARWINDS — The world’s most invasive and destructive cyberattack, to date.
By Andy Jenkinson — Guest Contributor | Group CEO Cybersec Innovation Partners
via IainFRASER.net/CYBERInsights
SME Cyber Insights
Google Indexed on 110624 at 09:10 CET
#SMECyberInsights #SMECybersecurityNews #Cybersecurity #WhitethornShield #InternetSecurity #Cybercrime #CyberInsurance #DNS #PKI
THREAT INTEL: SOLARWINDS — The world’s most invasive and destructive cyberattack, to date.
The day SolarWinds finally listened and realized their massive security oversight -13 May 2021.
The world’s most invasive and destructive cyberattack, to date, was discovered by Fireye at SolarWinds in December 2020. SolarWinds had unknowingly suffered a subdomain takeover and a DNS attack. Both exploited SolarWinds‘ poor security of their critical Internet Assets.
We reached out to Tim Brown, SolarWinds CISO and shared information of their exposure. Several months later many were addressed, albeit a tad late.
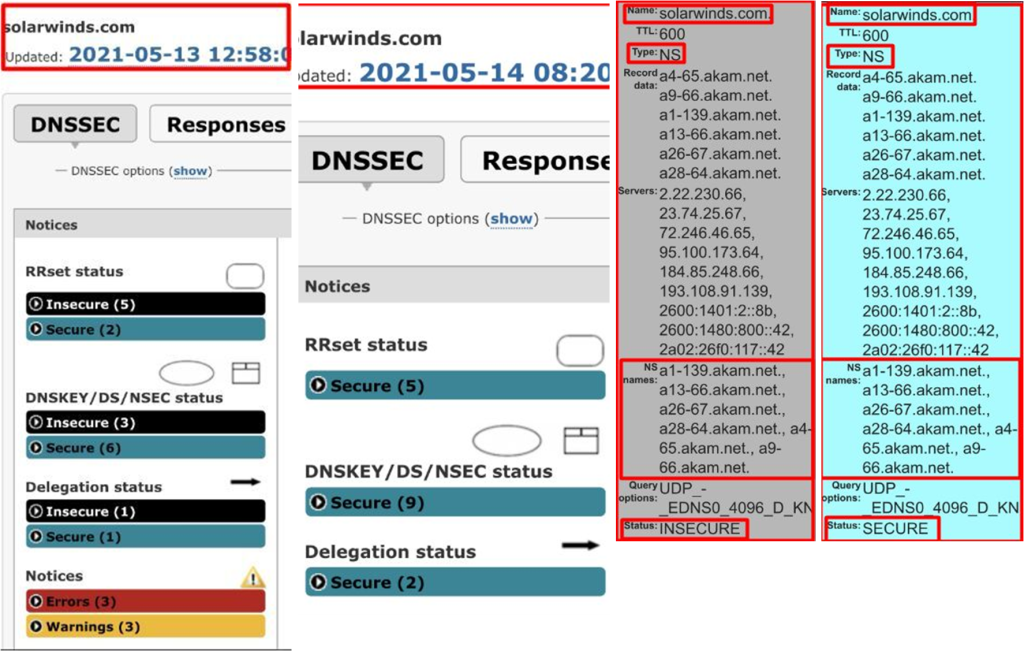
The DNS related attachments mean much more than is DNSSEC used or not. They provide a comprehensive overview and identification of the DNS and Servers in use:
1) INSECURE DNS records and Servers of SolarWinds dated 13 May 2021
2) SECURE DNS records and Servers of SolarWinds dated 14 May 2021
3) SECURE Named Servers of SolarWinds dated 14 May 2021
4) INSECURE Named Servers of SolarWinds dated 13 May 2021
On the 13/14 May 2021, 5 months after the discovery of the crippling, long term cyberattack, Tim Brown and SolarWinds finally addressed these DNS Named Servers.
The move from INSECURE DNS Named Servers, to SECURE DNS Named Servers marked a profound leap in resilience and security for SolarWinds.
Prof Bill Buchanan OBE FRSE wrote a paper on December 10 2015, ”The Most Fragile of Foundations of The Cyber Age — DNS”
Companies that collect, collate, harvest, and use large amounts of data whilst lacking control and management of their DNS are simply waiting and fueling Cybercrime.
The Will to Act, like ignorance, is a choice.
Sadly all too often poor choices on both fronts are made. When this occurs, companies and organizations remain exposed, vulnerable, and insecure. These companies greatly increase their chances to be added to the list of victims.
You can be Reactive to the Facts, as Tim Brown and SolarWinds were, or Proactive and address these critical Internet Assets and DNS servers.
FBI Cyber Division Federal Bureau of Investigation (FBI) The White House GCHQ National Cybersecurity Coordination Center (NCSCC) Information Commissioner’s Office U.S. Securities and Exchange Commission
About Andy Jenkinson
Group CEO CIP. Fellow Cyber Theory Institute. Director Fintech & Cyber Security Alliance (FITCA) working with Governments. Recognised Expert in Internet Asset & DNS Vulnerabilities.
Andy Jenkinson is a senior and seasoned innovative Executive with over 30 years’ experience
as a hands-on lateral thinking CEO, coach, and leader. A ‘big deal’ business accelerator, and
inspirational, lateral thinker, Andy has crafted, created, and been responsible for delivering
100’s £ millions of projects within the Cyber, Technical, Risk and Compliance markets for
some of the world’s largest, leading organisations. Andy has a demonstrable track record
of largescale technical delivery and management within many sectors including the
Professional, Managed, and Financial Services.